Microsoft Intune does not have any build in GUI way of deploying Google Chrome policies, but we can leverage of the ADMX-backed policy option in Windows 10 and Intune. I wrote a blogpost on “How does a custom set of ADMX-based policies work with Intune” when you get the hang on how it is working, it just requires a lot of patience and manual work. In this blog post I will not comment on the settings in policy settings – I have created the settings 1:1 from the recommendation and as is says when you download the GPO from IASE – Information Assurance Support Environment do not try this in your production environment it can cause loss of required functionality, for Intune if you do not have a Intune test environment you can import the policy and only assign it to a couple of test devices before deploying it brought.
First we need to find all the settings that are set in the GPO as recommended when download the policy there is a folder for each policy – and in this case we are looking for the DoD Google Chrome v1r14
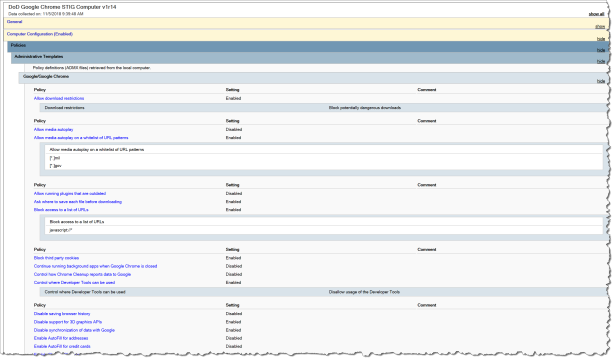
And in the report folder you find DoD Google Chrome STIG Computer v1r14.htm where you can see all the recommended settings
Then you need Chrome Browser for enterprise the link contains both the Google Chrome Enterprise MSI and the ADMX.
To be familiar with the settings to find the correct OMA-URI you need to look at 3 places:
- chrome.admx
- chrome.adml
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\AdmxDefault\Machine GUID\Chrome~Policy~googlechrome
All 3 places can be of help figuring out both the OMA-URI, and the String value, some settings is just <enabled/> or <disabling/> and other settings requires more information
In your environment you may need additional setting to get your environment running – one of the cases I see is:
In the default all browser extensions is blocked and that is always a good idea if you want completely control over what is running on your devices – but when we do MDM management of Windows 10 devices we often leverage AzureAD and Conditional Access and are running Windows Defender so there is some browser plugins that is need to have on the device – so if we are force installing them with another policy setting then it is allowed to run. The tree browser plugin I always uses are:
Where you need a extra policy settings
OMA-URI : ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome~Extensions/ExtensionInstallForcelist
Data type : String
Value : <enabled/>
<data id=”ExtensionInstallForcelistDesc” value=”1bkbeeeffjjeopflfhgeknacdieedcoml;https://clients2.google.com/service/update2/crx2ggjhpefgjjfobnfoldnjipclpcfbgbhl;https://clients2.google.com/service/update2/crx3ppnbnpeolgkicgegkbkbjmhlideopiji;https://clients2.google.com/service/update2/crx”/>
NOTE: “” are the characters used as separators and “2” where you need to change the first number when using a multi value policy setting even if there is only one entry.
Like this one where we are blocking “javascript://*”
OMA-URI : ./Device/Vendor/MSFT/Policy/Config/Chrome~Policy~googlechrome/URLBlacklist
Data type : String
Value : <enabled/> <data id=”URLBlacklistDesc” value=”1javascript://*”/>
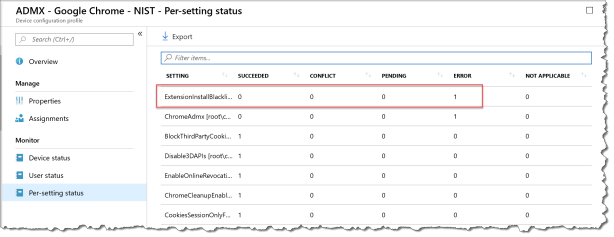
When you are creating the Intune profile with ADMX based policies some time you don’t get it right the first time you can see the error in the Intune console under Monitor – Per-Setting status
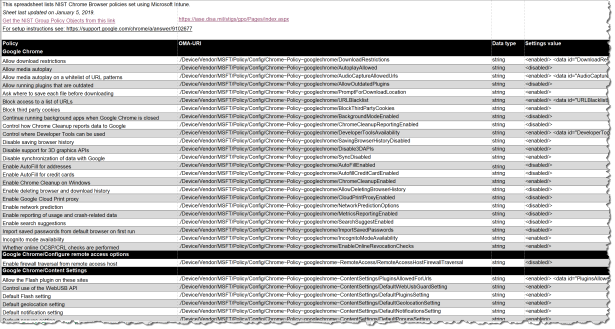
I have create a spreadsheet with all the settings – it can be downloaded from my Github page
The policy requires two different Google Chrome ADMX files : chrome.admx and GoogleUpdate.admx
There is only one setting in GoogleUpdate.admx that set the update frequency for Google Chrome
I have also created 2 powershell script to Create a Intune Windows 10 Custom policy profile that create all the setting in the Google Chrome ADMX based policies from STIG – it can be downloaded from my Github page there is two import file:
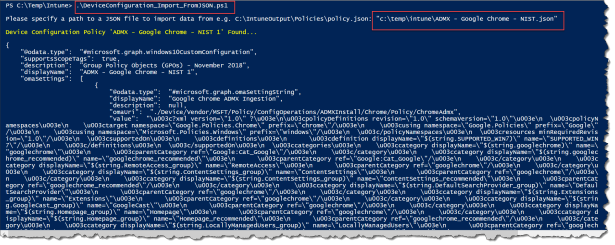
First you need to get the Intune json import script from @davefalkus Github page
Run the .\DeviceConfiguration_Import_FromJSON.ps1 and point to the .json file to import it.
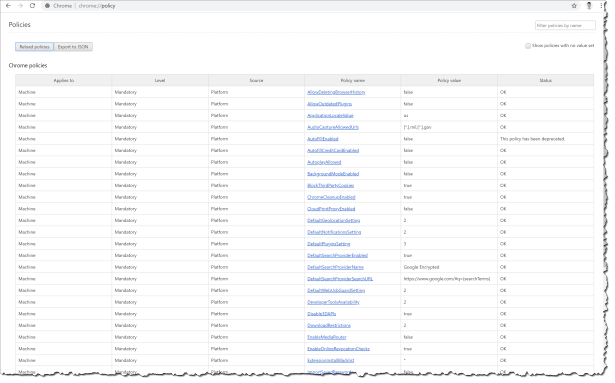
What is the end user experience
The end user will just have a more secure Google Chrome browser as the IT department have configured – if the end user is starting Google Chrome and are going to : chrome://policy/ then they will see the active policy
Read more:

Any ideas on how to set the homepage URL? I’m not seeing it in the NIST