With the release of Microsoft Intune 1901 we finally got MDM security baseline, the first time Microsoft talked public about this was at Ignite 2018, everybody I have talked to since has been waiting for this feature, in the waiting time we have been using other security baseline like the one from NCSC.
When doing Windows management today we need to look at the security part of hardening Windows. MDM security baseline is build based on Windows Security baseline it is more and more important to remove local administrator rights and create a baseline for securing your Windows Desktop. You don’t need to follow the Microsoft Security baseline, but it is a great starting point, then you can add or remove settings so that your users can still do there work and you line of business applications are working as expected.
This baseline is built as a generic infrastructure that allows IT admins to eventually import other security baselines based on CIS, NIST, and other standards. Currently, it’s available for Windows and will eventually include iOS and Android.
After Intune service release 1901 Security Baseline is in public preview for all tenants – so there is no excuse not to start testing it.

How to configure Windows 10 Security baseline in Intune
- Click on Security Baseline (Preview)
- Click on MDM Security Baseline for October 2018 (This security baseline is for Windows 10 1809)

- Click Create profile

- Enter a Name : Windows MDM Security Baseline for October 2018
- Click to expand settings

Then you can go expand all the category and see if all the settings is as you want.
Many of the settings are also to be found in other Intune profiles but many are also ADMX based policy settings that are now in the GUI in the security baseline an example is Internet explorer

There is other settings that are not configured that you maybe want to to use an example is in Windows Defender – if you are running 3 part. anti malware solution you may change some of the default configuration

If you are running Windows Defender you may to change Defender cloud block level from Not Configured

To Zero tolerance

When you have made your change so that the security baseline match your requirements you need to assign it.
- Click Policies created
- Click on the policy you just created
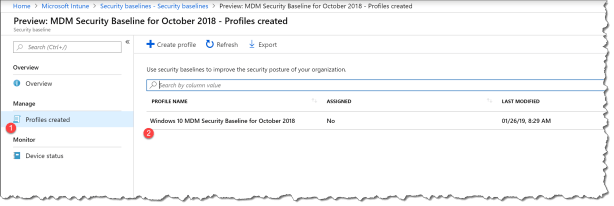
- Click Assignments
- Click Select groups to include and find your test group

How to monitor you security baseline
Like all other policies in Intune there is a overview when you have deploy a policy, in the security baseline case there is 4 state that a policy can be in:
- Matches baseline
- Does not match baseline
- Misconfigured
- Not applicable

On the device it self in Intune you got a new monitor area – Security baseline:
- Select the Security baseline
- Click Preview: MDM Security Baseline for October 2018
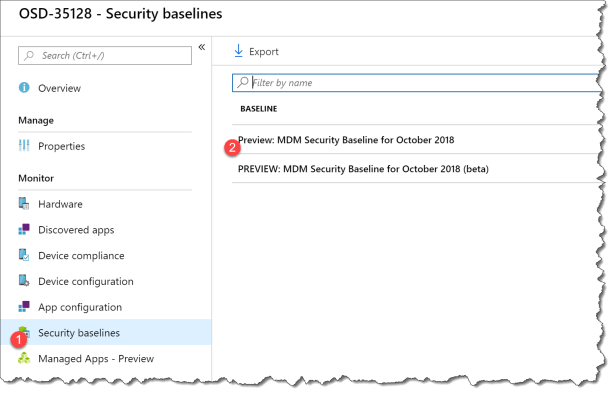
Then you can see all the settings name and you can expand them.
The easy way is to filter on the state so you are only looking for the settings that are not working as expected

Then you can expand the setting name
- Find the settings name that you want to see
- Only look for the Misconfigured in this case

You can also look at it from the security baseline policy it self in the monitor section

When you are looking in the Per-setting status it is easy to sort the setting after the status:
In this case after conflict

In this case error
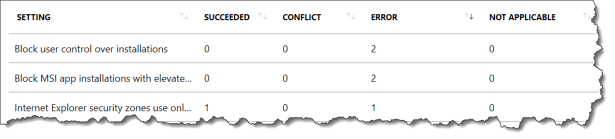
in this case not applicable
Then you can start changing you baseline or find the Intune profile where you have the setting configured.
At my first test on a AzureAD joined device with out any changes to the security baseline I was not able to login.

Happy testing 🙂
Read more:


Thanks for another write-up, but even though our tenant is at 1901, we do not have the Security Baseline menu-item.
According to this issue on Github it can take an additional week to appear (https://github.com/MicrosoftDocs/IntuneDocs/issues/1931)
How does one get into these early Previews?
I am trying to test this item but as of last week I get permission denied even though I am an InTune Admin.